Pivoting Basics - Part 1
[
HTB OSCP Pivoting Part 1, pivoting introduction and using SSHuttle
Part 2, pivoting with Chisel
Part 3, pivoting with Ligolo-ng
Pivoting Cheat Sheet, pivoting cheat sheet
Pivoting!? - Part 1
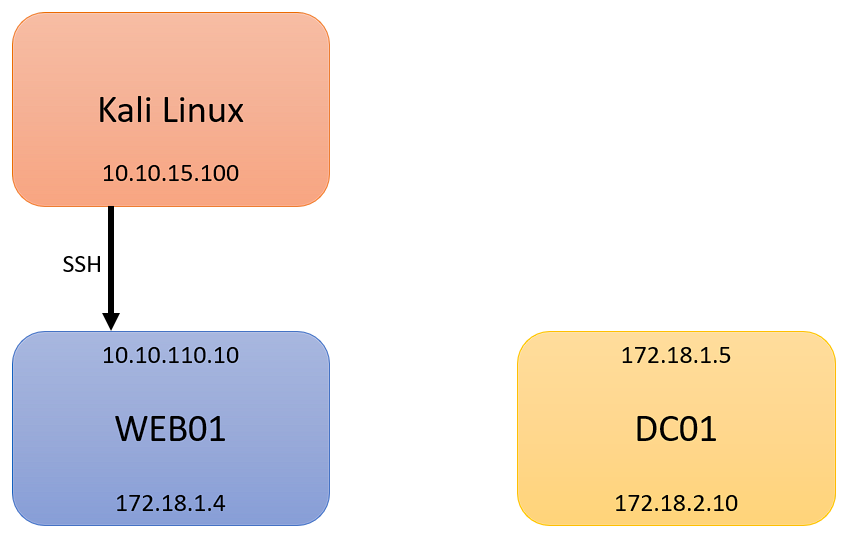
What the heck is pivoting? In short, it is a technique that is used after a foothold is gained on a target machine, and you wish to access a network that is otherwise not publically accessible, such as from a second internal network interface. For an example, let’s consider the following. Let’s imagine you have a web server, call it WEB01, with a public IP of 10.10.110.10, which you have compromised and have access to. If you wish to pivot to an internal network, 172.18.1.0/24, pivoting on the WEB01 box would provide you access to the internal 172.18.1.0/24, which you could then access on your Kali Linux machine.
For the following scenario, and for the rest of my walkthroughs, the following will remain true:
- Kali Linux (Attacking Machine): 10.10.15.100
- First Pivot Machine (Public IP): 10.10.110.10
- First Network: 172.18.1.0/24
- Second Network: 172.18.2.0/24
- Second Pivot Machine: 172.18.2.15
- Third Network: 172.18.3.0/24
- Third Pivot Machine: 172.18.3.20
To begin this tutorial, we have the ability to login to WEB01 with SSH credentials, using an id_rsa file. It can be a user, or admin/root, it does not matter. For Part 1, we wish to access DC01, located at 172.18.1.5:
SSHuttle
To start, imagine you want to pivot from WEB01, out the 172.18.1.4 interface, to enumerate DC01 on 172.18.1.5. As most HTB machines use SSH on their first foothold, I will assume a SSH id_rsa key is already discovered and available. The easiest tool, and my goto, is SSHuttle. It is baked into Kali Linux, but if you are not using Kali, it can be installed easily. Here is the GitHub for SShuttle.
1
sshuttle -r <username>@<ip_addr> <remote_network> -e 'ssh -i id_rsa_file'
The above command expects two parameters, -r and -e:
- -r : (also –remote) is the remote network you want to access
- -e : (also –ssh-cmd) is the ssh command to run. In this case, because we have an id_rsa file of the victim user, we use the basic ssh’s -i flag
Our command would thus look like:
1
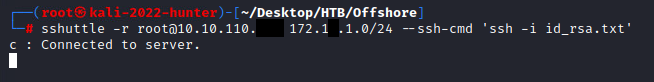
sshuttle -r root@10.10.110.10 172.18.1.0/24 -e 'ssh -i id_rsa.txt'
If all is correct, we will receive ‘c : Connected to Server’:
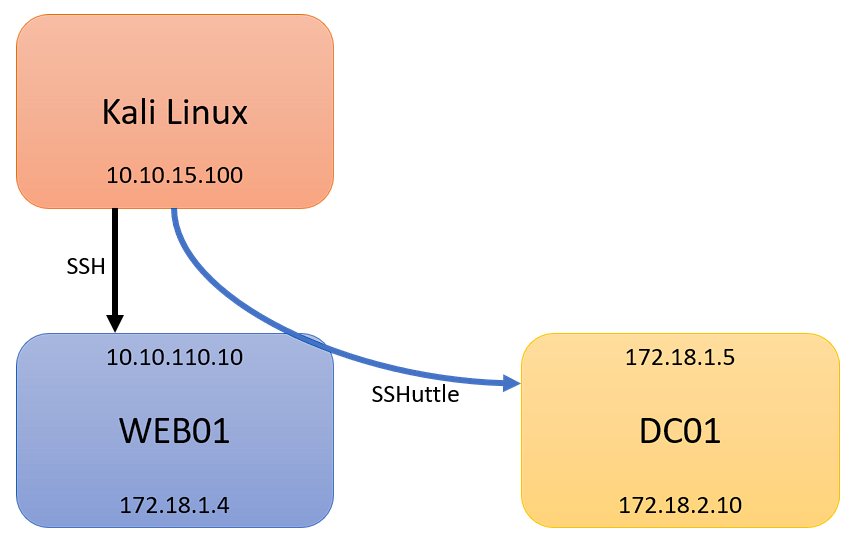
We would now have access to the first subnet, 172.18.1.0/24, and also where DC01’s interface 172.18.1.5 resides. We could now continue with enumeration of the new network. Our network diagram would appear like:
And as a bonus, if we wisht to begin enumerating, with NMAP, we could use the following command:
1
nmap -Pn 172.18.1.5
However, because we are going through a tunnel, we would not be able to use the full suite of scans available from NMAP, such as NSE.
[HTB OSCP Pivoting